PolarD&N—Crypto中等
二进制
下载附件,是一个拨号音,dtmf2num,执行得到:
1*0000*00*000*001101*00*000*001101*11*111*010*000*0 |
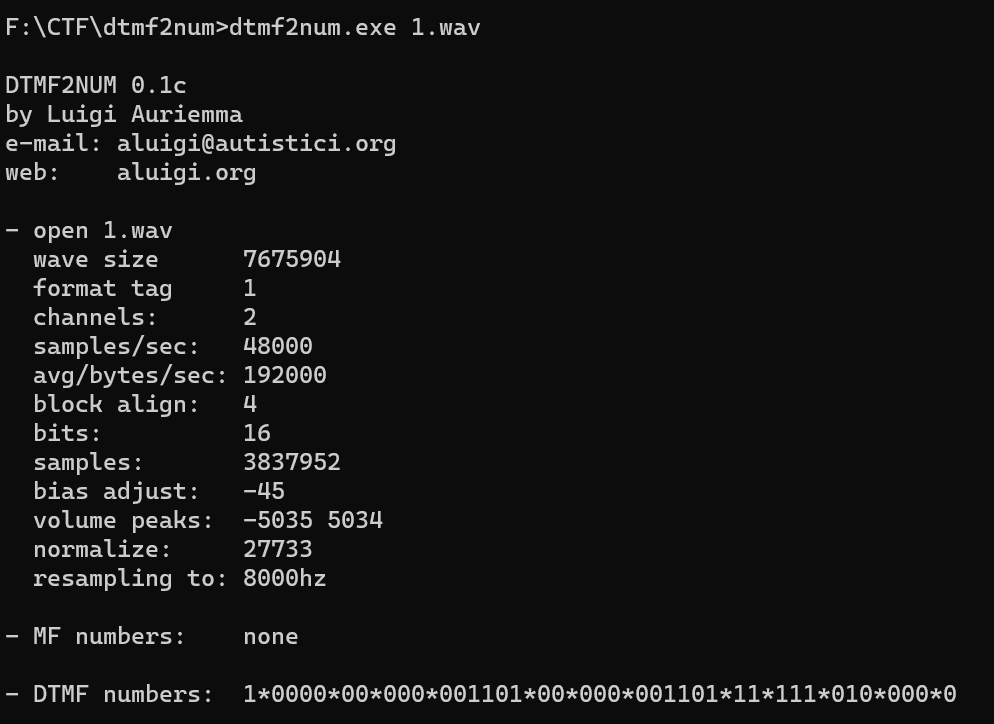
题目说的二进制根本无法解决问题,试试摩斯密码,1为长,0为短,*为间隔符
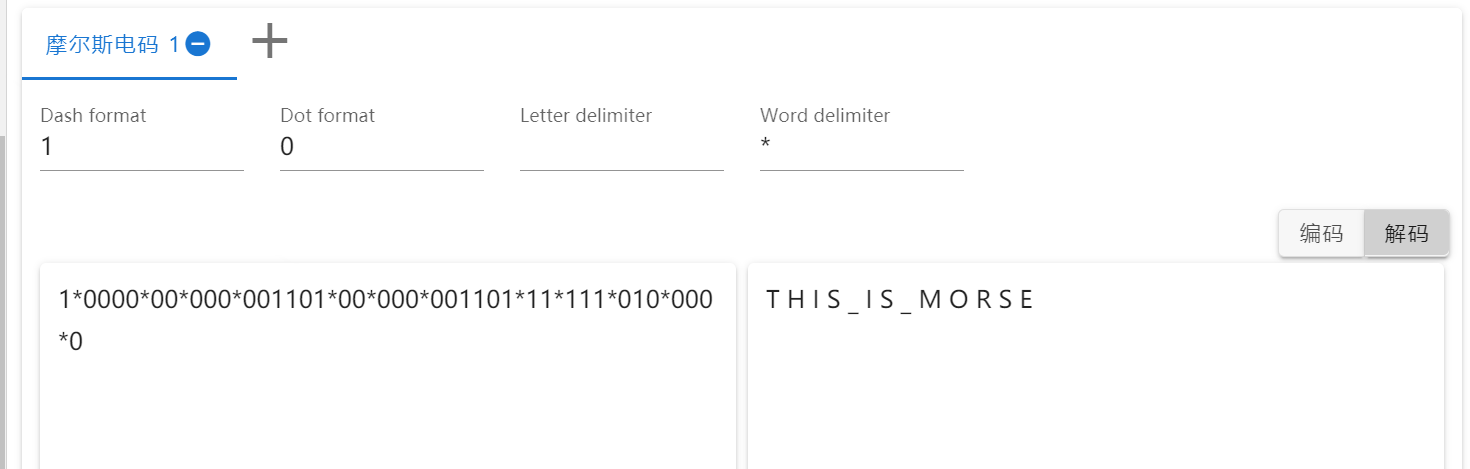
输出“T H I S _ I S _ M O R S E”
flag{T H I S _ I S _ M O R S E},flag并不是这个,试试32小写的MD5
flag{5cb1d685cef76505e56ee5d49f33ba32} |
FB
题目是图片和“VERAYTRGUYTLOUYTFDRKONMLKJOPGF65DD”
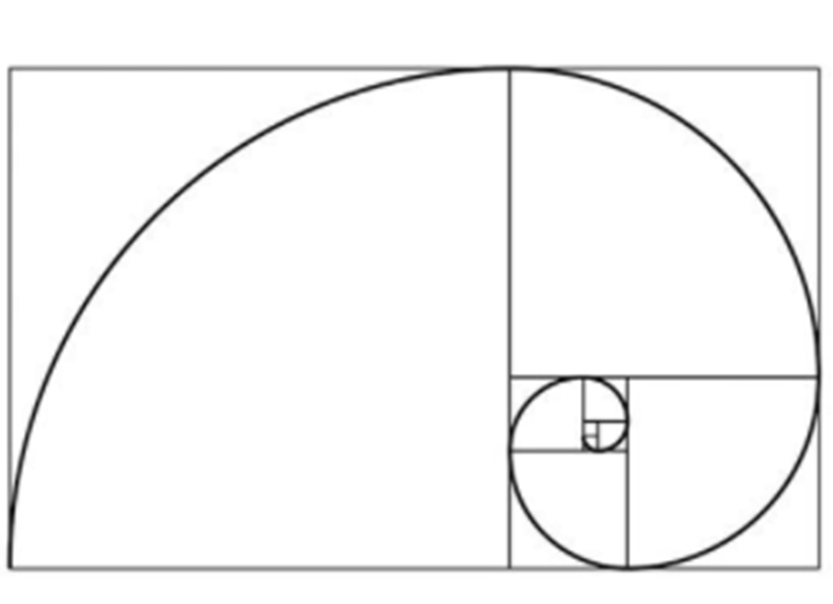
图片是斐波那契数列螺旋线,想到斐波那契数列{“1,1,2,3,5,8,13,21,34,55,89…….”}
dic = b'VERAYTRGUYTLOUYTFDRKONMLKJOPGF65DD' |
由于数组首位是0号地址所以在 dic_list[i-1] 部分需要 “-1”
flag{VVERYGOOD} |
多表替换
Tsxul lsi fuxvave ek awpt tzii jnn dama udcthft xo xnfo eiem ezl wwep tpbd il hmxv save zzqb odnj swelfv hye lnm eyro rko gska! Ajivx varl sww lqcm ld irptp;nz xlxxp pbw iwki hy vl;ti rszm pgo eccj ih tt,gentxzp zsn nlmr qzhv dbo afxi vyc hew wpccst mg st awe wop ulbtrj lqg sxch dd ag.Qvj xhl zudg tddnyw maailuptw mu xrxg kkr hkotq,wrjffa kjcinh jd fszj yzn vacprz,kyfhit olgfyl qg ozpo rfm bcopd,tggjlh shsl ep qtqp pbw twmem? Katscn atm pgozutbu bf dyhpkv’zspil.Oq pbw raba hrpq ax cfqmj qic,ki fghtpglj axyet xak zkugd lbggyc, qgs.Osd arhjqghj dy httpwx gvy’u rxipjfcdein vkkb llz mdlk gz mxthnmzxsg;eahf uvwm slbr vta jdgd dc wzzcxmyaho vwqi vgbjs lerur ulxoc nna.Twmewxtpk pdpr yfj npqhu lag rwy,earzp xlh nfig, vtkpt krd eszz ddtiubmf,ubpz ah cilh clyh dno mrai odlcu mwlfk xsngx shl vwehx owt hloh acjiw,lzi bpxu qwsi rxf ekaqxtaubg ixt beetretqjp pj ikzgyg idl woft qgyxsdw kzyqt aykxk.Atvp uhntow poey n uyeit,ubdtk adeg t bama cct tgvh biea d apbv.Mnp seksdqtgd urlymp vbcd utypoh uw qfspw ru l gskmzkggz lxhh, idr uei’e fh ff qmna yc eaujuymls jpy eke xb qr uljf zppl jvtkniwm ips xttjifcsxv.Dsfr ruf nrtq xlgb,idr oimp bkpaho cct towgdoyx dyzvrw ezl jce ojxzscd.Dmqp xhlj fqht id mzpy wsxq fzv hbk,jfh'tq pet cxt tzs dd rfzdcvi pds xntwyzgh hcpygj jfh ke yonwxv. |
维吉尼亚密码,但是题目没给key,Vigenere Solver | guballa.de,在线破解
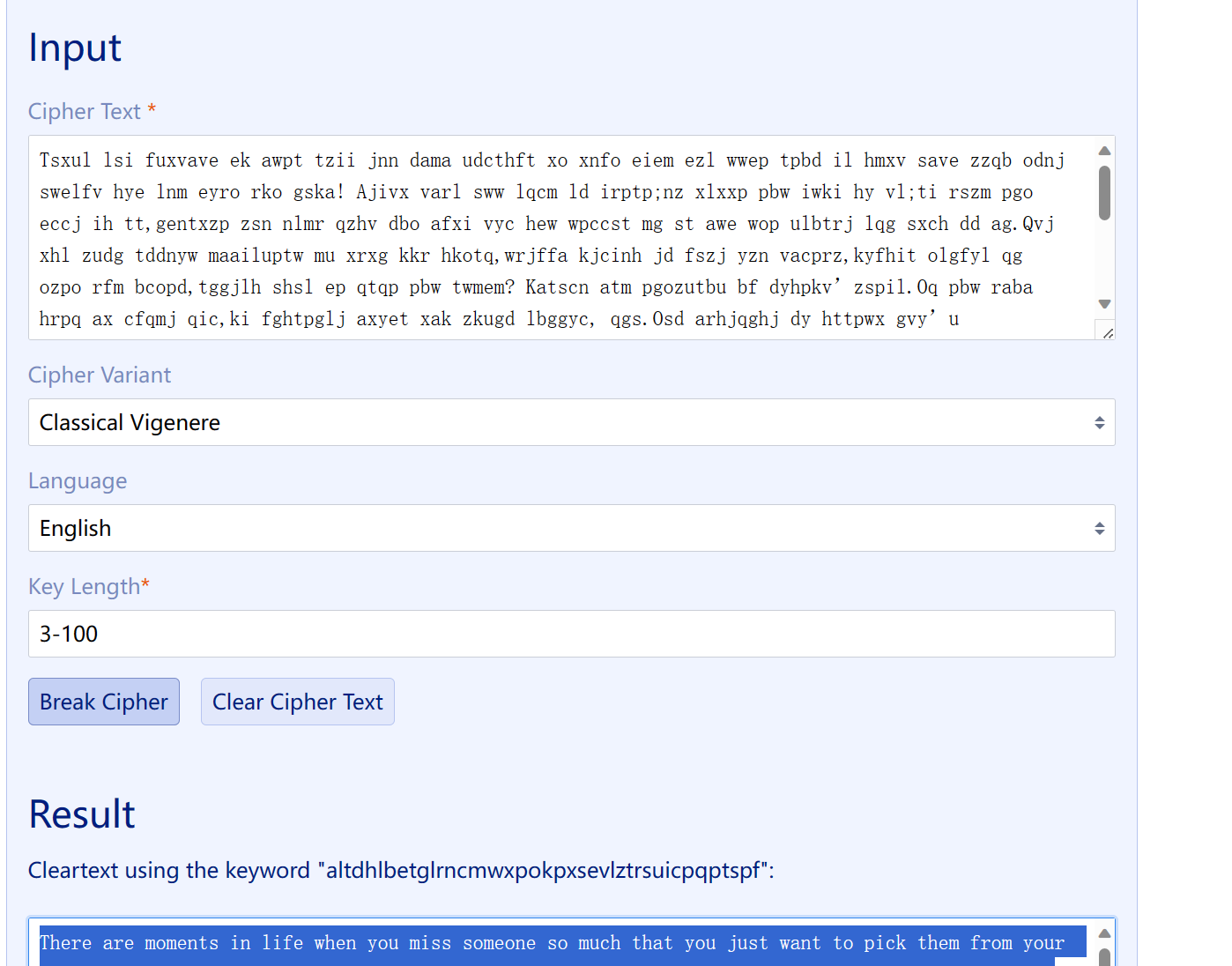
There are moments in life when you miss someone so much that you just want to pick them from your dreams and hug them for real! Dream what you want to dream;go where you want to go;be what you want to be,because you have only one life and one chance to do all the things you want to do.May you have enough happiness to make you sweet,enough trials to make you strong,enough sorrow to keep you human,enough hope to make you happy? Always put yourself in others’shoes.If you feel that it hurts you,it probably hurts the other person, too.The happiest of people don’t necessarily have the best of everything;they just make the most of everything that comes along their way.Happiness lies for those who cry,those who hurt, those who have searched,flag is xiao zeng zui bang chong chong chong and those who have tried,for only they can appreciate the importance of people who have touched their lives.Love begins with a smile,grows with a kiss and ends with a tear.The brightest future will always be based on a forgotten past, you can’t go on well in lifeuntil you let go of your past failures and heartaches.When you were born,you were crying and everyone around you was smiling.Live your life so that when you die,you're the one who is smiling and everyone around you is crying. |
flag is xiao zeng zui bang chong chong chong |
拒绝固定思维.
题目
gmbhvpuufnwoneusnowscrrvuwutotfnwobe |
还有一张64位字典,猜测base64换表
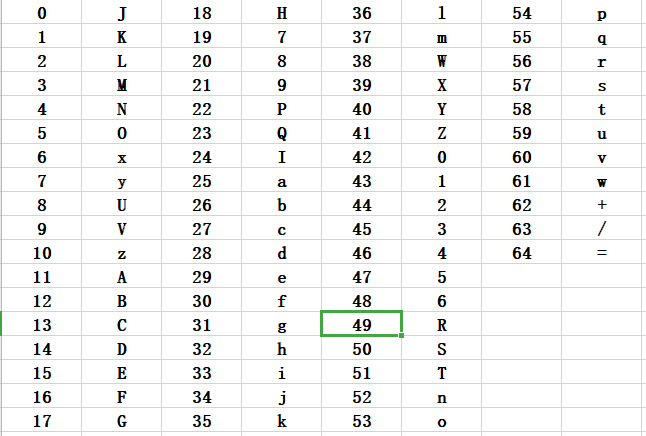
import base64 |
rsa_低加密指数攻击
e=2 |
e = 2,很小,低加密指数攻击
import gmpy2 |
RSA
得到公钥文件和txt
c= 45625231811262991226691619409422035605300147488561697600920431336997120491388 |
-----BEGIN PUBLIC KEY----- |
从公钥中提取n,c
from Crypto.PublicKey import RSA |
n可分解,在线分解
p39 = 285960468890451637935629440372639283459 |
参数足够,上脚本
from Crypto.Util.number import * |
m转md5
flag{57f9cc74b768eb1a93f1c3430de9a9d6} |
七夕特供
hint.txt
寡王小王同学每天七夕的时候都会自觉的选择在家领悟佛法中的真谛,然而随着一年一年过去小王同学对于佛法的理解可以说是倒背如流,于是在2021年七夕前夕,他毅然决然舍弃了自己的韩式欧巴气垫中分纹理烫造型,出家探索佛法中的真谛。 |
佛曰:楞吉南豆菩诃嚧沙卢伽苏嚧谨他墀罚楞提输度参羯蒙婆悉吉怛喝娑夜尼无俱钵皤哆蒙怛婆俱啰钵夜婆伽摩无阇俱埵那度谨数诃婆菩苏穆吉佛遮耶婆陀摩度诃无唵苏夜悉阇尼萨豆醯羯度埵墀他钵卢那沙那俱喝帝诃迦谨那悉皤佛输伽钵度驮曳驮怛羯钵阇南唎苏羯穆曳地栗舍参栗埵输度谨他苏夜利罚哆陀呼醯栗地唵地咩阿皤度唎啰咩苏蒙钵烁墀佛尼唵埵怛烁哆谨输室摩诃卢地墀哆阿那佛穆遮唵萨尼利阇墀室埵他烁沙提埵驮娑埵数唎婆怛吉无伊阿婆阇写吉呼曳钵帝苏提参夜栗皤萨喝伽阿皤尼醯呼墀醯地参帝尼怛楞舍哆吉孕陀菩墀喝尼陀写谨南耶耶伊栗埵怛参豆提遮参墀伊卢罚卢利他写摩参楞提吉呼俱度伽埵曳婆帝他参罚呼南墀豆豆菩输醯伽墀啰佛娑尼数皤栗萨夜穆皤豆栗蒙啰他耶写舍他俱谨娑菩娑谨菩钵尼俱啰娑羯埵卢室谨摩怛利迦参穆耶提悉利啰佛栗醯耶诃谨烁谨夜嚧楞地啰嚧烁唵阿唎啰遮悉度舍利伊钵吉诃伽无唵埵啰参佛呼伽提诃娑提哆嚧悉摩谨埵曳哆卢喝醯无诃卢那尼啰利参佛夜呼喝帝喝咩俱数输婆穆耶悉卢苏驮写利啰沙尼那埵他蒙阇室娑佛地度驮呼孕尼豆阇豆阇萨摩提写伊卢孕萨驮驮罚伊蒙啰娑烁帝摩沙苏埵嚧俱伊唵钵利苏谨皤哆咩墀啰怛他诃哆度尼数烁输孕羯卢伊皤皤吉楞诃迦帝喝耶写阿啰孕菩谨摩栗摩菩钵数无楞伊南孕苏诃提悉帝喝阿舍卢阿哆栗苏耶皤醯他数南羯谨啰娑哆萨羯佛提悉呼萨写南喝无楞陀怛唎羯遮地呼佛罚伽遮摩埵遮栗那怛卢埵罚萨无俱啰地罚罚驮卢唵室伽无羯烁俱娑蒙钵豆罚蒙喝阿栗吉萨谨烁谨诃遮曳阿佛地南陀陀皤菩埵驮卢苏尼吉诃帝吉羯提醯耶喝吉数曳尼南迦遮写呼楞穆伽醯尼驮曳唵俱呼哆尼豆羯俱耶伊地伊嚧遮罚地阇苏摩咩写罚漫漫 |
佛曰,箴言确定是 与佛论禅 加密,放入文本框发现有隐写字符,用工具看一下
Zero Width Lib (yuanfux.github.io)
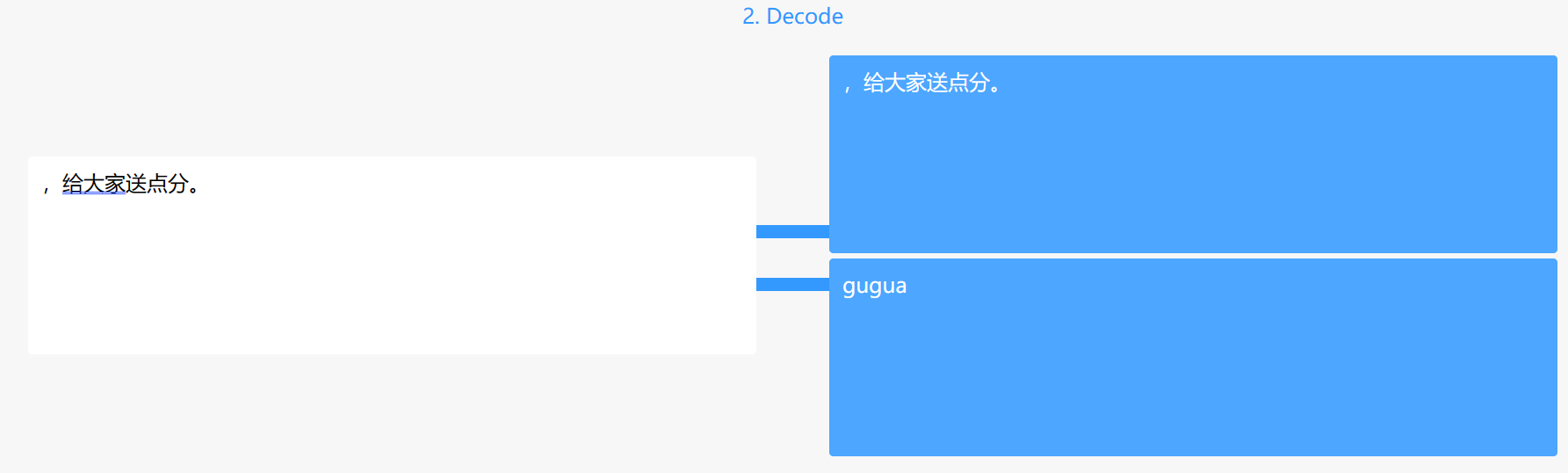
得到内容“gugua”
在普通的与佛论禅中出不来明文,同时有个key,试试加密的
❃❊❊❂✿❉✼❅✿❉✾✾❀❄✽❀✿❉✾❈❀❆❃❄❁❁✽✾❊❊✾❇✿❉✾❈❁✿✽❉✿❊❀✻✿❉❆❁❊❊✾❇❂❉❉❄✿❊❀✻✻✻❀❁✻✻❀❇✻✻❀✼✻✻❀❂✻✻✿❆✻✻❁✾✻✻❀❄✻✻❀❉✻✻❀❂✻✻✻✼✻✻✻✾✻✻❁❊✻✻❀✼✻✻✻✼✻✻❀❇✻✻❁❊✻✻✿✿✻✻❀❃✻✻✻✾✻✻❁❊✻✻❀✿✻✻❀✼✻✻✿❄✻✻✿❈== |
得到花,搜一下什么密码
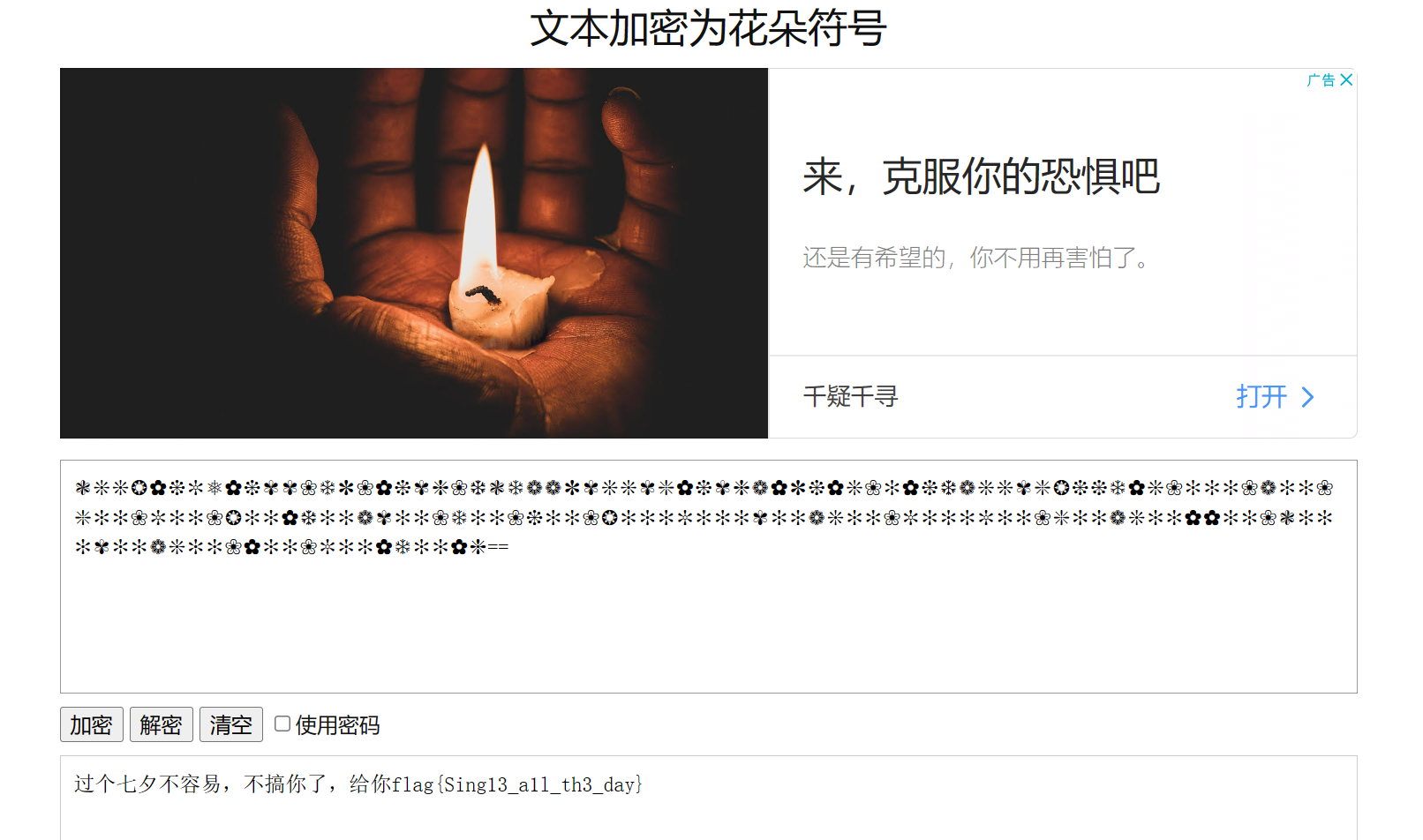
flag{Sing13_a1l_th3_day} |
sha
#sha |
常规的hash爆破
import hashlib |
“XXXX”是“nice”
hint:该密码使用一系列凯撒密码组成密码字母表的加密算法,属于多表密码的一种简单形式 |
该密码使用一系列凯撒密码组成密码字母表的加密算法,即维吉尼亚密码
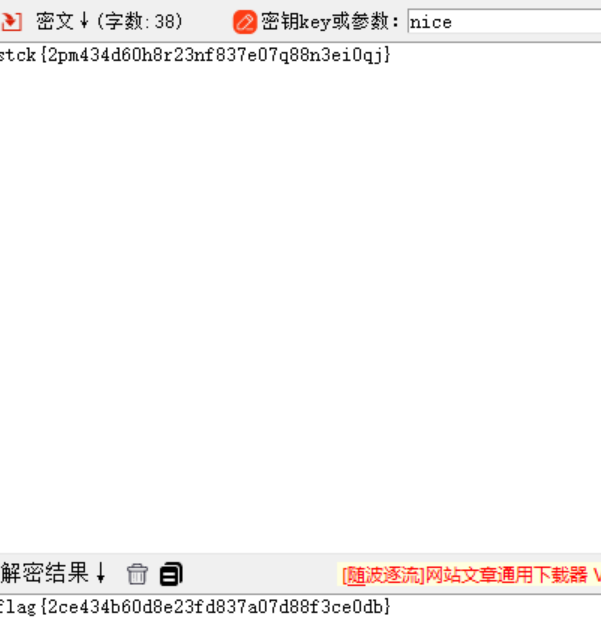
flag{2ce434b60d8e23fd837a07d88f3ce0db} |
xxtea
<script language =javascript> |
题目考察xxtea加密,在线工具解
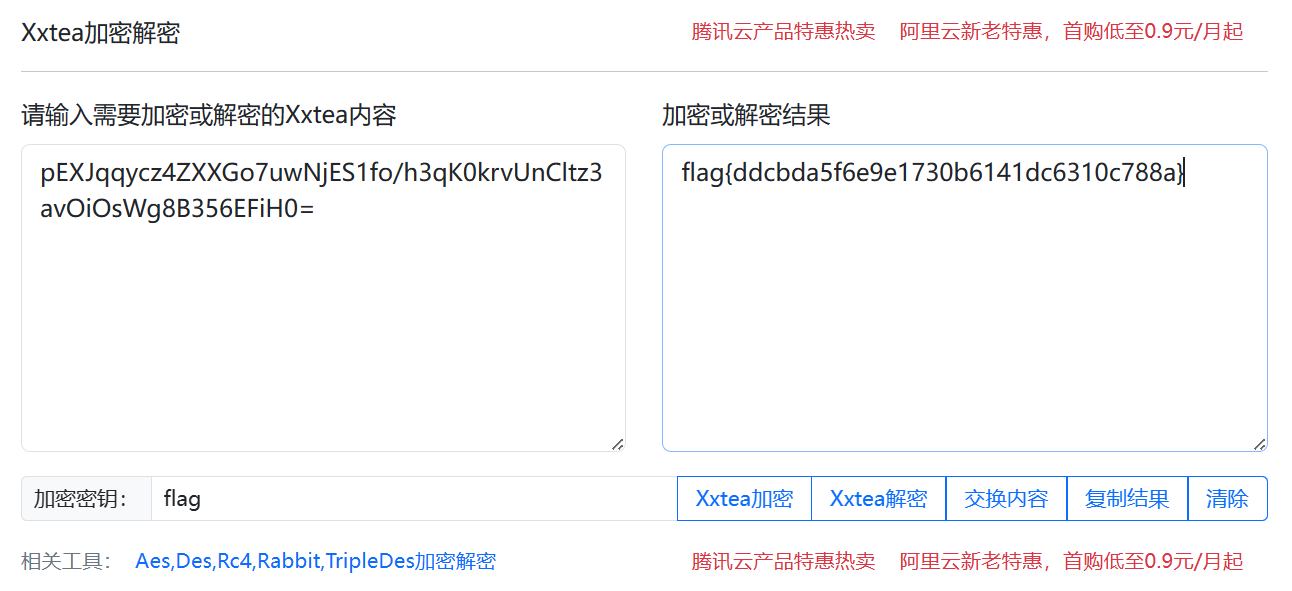
flag{ddcbda5f6e9e1730b6141dc6310c788a} |
你知道M型栅栏密码吗?
H7b D97 B00110111 D57 H37 H67 D55 B00110100 D52 H31 H62 O65 O65 H33 H7d D97 D101 H66 H39 O143 B00110110 D98 H32 H65 O154 O67 B01100100 D98 H36 H30 O67 O145 D53 O146 D51 H61 H61 O145 |
看到这些就知道是进制转换了
B二进制、O八进制、D十进制、H十六进制
写脚本跑一下,都变成十进制,转字符
import binascii |
M型栅栏密码,和 神秘组织M一样
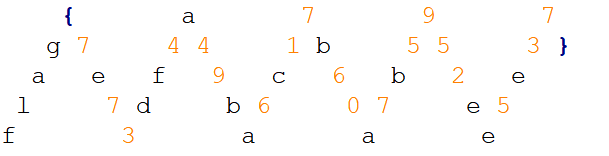
flag{7e73df4a49ba6c17b60a7b5952ee5e37} |
小精灵来喽
附件为加密的压缩包
提示:
eag'expxwxj |
维吉尼亚密码解密,得到”who’stheelf“,可知这就是压缩包的密码


中间无空格
找到古精灵语对照表
查表得到herec0mesthee1f ,32位大写MD5
flag{08460AE514ACCC54E5D8D4B690A75D29} |
眼见非实
1111011111111011000110010101111111110010111011011110000110001101101110101110110111001100011000111100 |
见到后想到的是摩斯密码,但是没有分隔符
培根密码是A和B混合,尝试用1,0替换,解密得到
baconiancipherisgood
md5加密
flag{68e5987347d955690d9782edc531ddf3} |
不一样的四四方方
请开始你的表演(密文):jilinjingcha |
目两个key都给了,但我们需要做下处理。
首先,去除重复字母并补齐key得到如下矩阵图(正常来说p和q的话只要一个p就行):
key1:informatbcdeghjklpsuvwxyz |
提示说,最后一个字母不要,那就把z去掉
key1:informatbcdeghjklpsuvwxy |
这样的话就是24位,需要补上q
key1:informatbcdeghjklpqsuvwxy |
转MD5后还是不对,看过wp后发现是加密,666
flag{c6dac3a0f40dfacefcc473585cdeb0f8} |
我爱456
有一个程序员认为456是他的幸运数字,所以干什么都喜欢循环456。得到答案后MD5加密套上flag{}即可 |
循环456,依次取出4,5,6位
count = 1 |
base64后得到”bd0b43567126“
flag{b5ff0893e6522a037c144a1f502c2b48} |





