beginCTF2024
*为赛后复现
虽然但是,我还是厚着脸皮报了个新生赛道😊😢,不过(就不去自由赛道丢人了)
MISC
real check in
真签到,base64即可
tupper
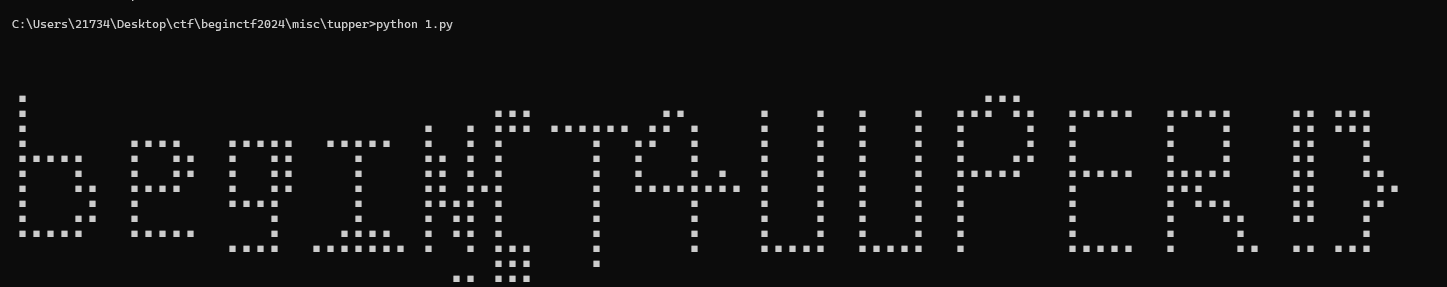
附件给了好多txt文件,而且文件名也给了顺序,直接合并文件,得到
MTQyNzgxOTM0MzI3MjgwMjYwNDkyOTg1NzQ1NzU1NTc1MzQzMjEwNjIzNDkzNTI1NDM1NjI2NTY3NjY0Njk3MDQwOTI4NzQ2ODgzNTQ2NzkzNzEyMTI0NDQzODIyOTg4MjEzNDIwOTM0NTAzOTg5MDcwOTY5NzYwMDI0NTg4MDc1OTg1MzU3MzUxNzIxMjY2NTc1MDQxMzExNzE2ODQ5MDcxNzMwODY2NTk1MDUxNDM5MjAzMDAwODU4MDg4MDk2NDcyNTY3OTAzODQzNzg1NTM3ODAyODI4OTQyMzk3NTE4OTg2MjAwNDExNDMzODMzMTcwNjQ3MjcxMzY5MDM2MzQ3NzA5MzYzOTg1MTg1NDc5MDA1MTI1NDg0MTk0ODYzNjQ5MTUzOTkyNTM5NDEyNDU5MTEyMDUyNjI0OTM1OTExNTg0OTc3MDgyMTkxMjY0NTM1ODc0NTY2MzczMDI4ODg3MDEzMDMzODIyMTA3NDg2Mjk4MDAwODE4MjE2ODQyODMxODczNjg1NDM2MDE1NTk3Nzg0MzE3MzUwMDY3OTQ3NjE1NDI0MTMwMDY2MjEyMTkyMDczMjI4MDg0NDkyMzIwNTA1Nzg4NTI0MzEzNjE2Nzg3NDUzNTU3NzY5MjExMzIzNTI0MTk5MzE5MDc4MzgyMDUwMDExODQ= |
显然是base64解码
14278193432728026049298574575557534321062349352543562656766469704092874688354679371212444382298821342093450398907096976002458807598535735172126657504131171684907173086659505143920300085808809647256790384378553780282894239751898620041143383317064727136903634770936398518547900512548419486364915399253941245911205262493591158497708219126453587456637302888701303382210748629800081821684283187368543601559778431735006794761542413006621219207322808449232050578852431361678745355776921132352419931907838205001184 |
万能的搜索引擎找到了塔珀自指公式,在终端运行
from functools import reduce |
下一站上岸
- 某同学在考公的时候看到这样一道题,发现自己怎么也找不到图形的共同特征或规律你能帮帮他吗?
一张图片什么都不知道,放入010看看
解码得到
5o+Q56S6OuaRqeaWr+WvhueggQ== |
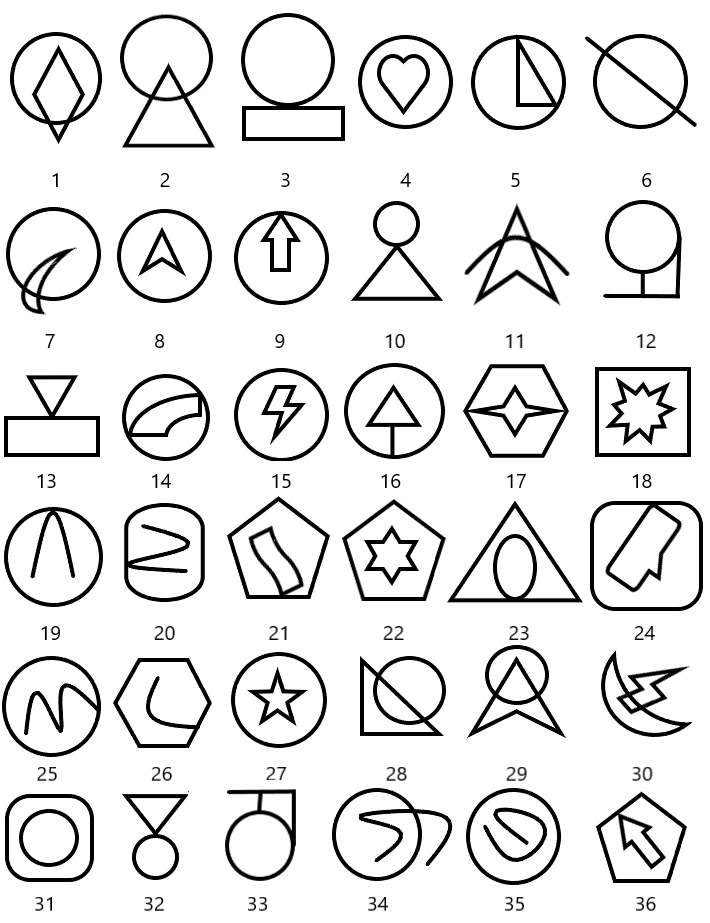
接下来就是区分长短空了,观察发现和交点个数有关。一个交点短,两个交点长,没有交点分隔符。
--. --- ..--.- .- ... .... --- .-. . |
所以flag:begin{go_ashore}
devil’s word
真·魔鬼语言,温州话
leu lia leu ng leu cai leu jau leu e cai b cai jau sa leng cai ng ng f leu b leu e sa leng cai cai ng f cai cai sa sa leu e cai a leu bo leu f cai ng ng f leu sii leu jau sa sii leu c leu ng leu sa cai sii cai d |
做这个题到处问温州的朋友,都说太抽象了,看不懂思密达。后来有个温州兄弟说和数字发音有点像,我可以朝这个方向试试看,试了一下,可不就是吗
from Crypto.Util.number import * |
你知道中国文化嘛1.0
4KMLHYUYWTRJRNPCTCZOFGFQ4KMLLYUYWLRJRNPCTC2OFGFT4KMLJYUYW3RJRMXCTC26FGFV4KMLFYUYWTRJRM7CTCZ6FGFU4KMLNYUYWLRJRMXCTC3OFGFS4KMLBYUYW7RJRM7CTC2OFGFW4KMLFYUYWPRJRMHCTCZOFGFR4KMLNYUYWPRJRNHCTC26FGFS4KMLBYUYWXRJRMXCTC26FGFU4KMLHYUYWTRJRNXCTCZOFGFV4KMLLYUYWLRJRNHCTCZ6FGFT4KMLJYUYWXRJRMXCTCZOFGFS4KMLFYUYWHRJRNHCTCZ6FGFV4KMLBYUYWLRJRNXCTCYOFGFS4KMLFYUYWDRJRM7CTC2OFGFV4KMLFYUYWDRJRNPCTCZOFGFV4KMLJYUYWPRJRNHCTC3OFGFS4KMLLYUYWXRJRMXCTC2OFGFT4KMLHYUYWTRJRNPCTCZOFGFX4KMLDYUYWLRJRNXCTCZ6FGFT4KMLJYUYW7RJRMXCTC26FGFV4KMLFYUYWHRJRMPCTCZ6FGFU4KMLNYUYWLRJRMXCTC3OFGFS4KMLBYUYW7RJRM7CTC2OFGFW4KMLFYUYWPRJRMHCTCZOFGFR4KMLNYUYWPRJRNHCTC26FGFS4KMLDYUYW7RJRMXCTCY6FGFT4KMLHYUYWTRJRNPCTCZOFGFS4KMLNYUYWLRJRMHCTC2OFGFT4KMLJYUYW3RJRMXCTC3OFGFT4KMLFYUYWLRJRNPCTCZ6FGFU4KMLNYUYWLRJRNXCTCZOFGFS4KMLPYUYWPRJRM7CTC2OFGFV4KMLFYUYWLRJRMXCTCZOFGFR4KMLJYUYWPRJRNPCTCYOFGFS4KMLNYUYWDRJRMXCTCZOFGFQ4KMLHYUYWTRJRNXCTCZOFGFW4KMLHYUYWLRJRMXCTC26FGFT4KMLJYUYW3RJRMXCTC3OFGFS4KMLFYUYW7RJRM7CTCZ6FGFU4KMLLYUYWLRJRMHCTC26FGFS4KMLLYUYWTRJRM7CTC2OFGFW4KMLFYUYWXRJRNPCTCZOFGFU4KMLHYUYWPRJRNHCTC3OFGFS4KMLFYUYW3RJRMXCTCYOFGFX4KMLHYUYWTRJRNXCTCZOFGFT4KMLBYUYWLRJRMPCTC3OFGFT4KMLJYUYWXRJRMXCTCYOFGFV4KMLFYUYWXRJRNHCTCZ6FGFU4KMLNYUYWLRJRNPCTC26FGF$4KMLJYUYWPRJRM7CTC2OFGFV4KMLFYUYW7RJRMPCTCZOFGFW4KMLHYUYWPRJRNHCTC36FGFS4KMLLYUYWXRJRMXCTCY6FGFR4KMLHYUYWTRJRNPCTCZOFGFQ4KMLLYUYWLRJRNPCTC2OFGFT4KMLJYUYW3RJRMXCTC26FGFV4KMLFYUYWTRJRM7CTCZ6FGFU4KMLLYUYWLRJRN7CTCY6FGFS4KMLNYUYWPRJRM7CTC2OFGFX4KMLFYUYWXRJRNPCTCZOFGFR4KMLDYUYWPRJRNHCTC26FGFS4KMLFYUYWLRJRMXCTCY6FGFU4KMLHYUYWXRJRMHCTCZOFGFW4KMLBYUYWLRJRMXCTCYOFGFT4KMLJYUYW7RJRMXCTCY6FGFQ4KMLFYUYW3RJRMPCTCZ6FGFU4KMLLYUYWLRJRM7CTCZ6FGFS4KMLPYUYWXRJRM7CTC2OFGFV4KMLFYUYWDRJRNPCTCZOFGFV4KMLJYUYWPRJRNHCTC3OFGFS4KMLLYUYWXRJRMXCTC2OFGFT4KMLHYUYWTRJRNPCTCZOFGFX4KMLDYUYWLRJRNXCTCZ6FGFT4KMLJYUYW7RJRMXCTC26FGFV4KMLFYUYWHRJRMPCTCZ6FGFU4KMLLYUYWLRJRMXCTCZOFGFS4KMLDYUYWTRJRM7CTC26FGFQ4KMLFYUYW3RJRMHCTCZOFGFS4KMLBYUYWPRJRNHCTC26FGFS4KMLFYUYWLRJRMXCTCY6FGFU4KMLHYUYWXRJRMHCTCZOFGFW4KMLBYUYWLRJRMXCTCYOFGFT4KMLJYUYWXRJRMXCTCYOFGFV4KMLFYUYWXRJRNHCTCZ6FGFU4KMLNYUYWLRJRNPCTC26FGFS4KMLJYUYWPRJRM7CTC26FGFQ4KMLFYUYWDRJRN&CTCZOFGFV4KMLFYUYWPRJRNHCTC36FGFS4KMLFYUYWTRJRMXCTC3OFGFR4KMLHYUYWTRJRNPCTCZOFGFS4KMLFYUYWLRJRMPCTC2OFGFT4KMLLYUYWDRJRMXCTC3OFGFQ4KMLFYUYWLRJRMHCTCZ6FGFU4KMLPYUYWLRJRMPCTCYOFGFS4KMLNYUYWHRJRM7CTC2OFGFV4KMLFYUYWPRJRM7CTCZOFGFX4KMLLYUYWPRJRNHCTC26FGFS4KMLFYUYWLRJRMXCTCY6FGFU4KMLHYUYWXRJRMHCTCZOFGFW4KMLBYUYWLRJRMXCTCYOFGFT4KMLJYUYWXRJRMXCTC26FGFX4KMLFYUYWHRJRNHCTCZ6FGFU4KMLLYUYWLRJRN&CTC2OFGFS4KMLPYUYWLRJRM7CTC2OFGFV4KMLFYUYWLRJRMXCTCZOFGFR4KMLJYUYWPRJRNPCTCYOFGFS4KMLNYUYWDRJRMXCTCZOFGFQ4KMLHYUYWTRJRN7CTCZOFGFR4KMLBYUYWLRJRNXCTCY6FGFT4KMLJYUYWXRJRMXCTCZ6FGFT4KMLFYUYW7RJRNPCTCZ6FGFU4KMLLYUYWLRJRMHCTC26FGFS4KMLLYUYWTRJRM7CTC2OFGFW4KMLFYUYWXRJRNPCTCZOFGFU4KMLHYUYWPRJRNHCTC26FGFS4KMLBYUYWXRJRMXCTC26FGFU4KMLHYUYWTRJRNXCTCZOFGFV4KMLLYUYWLRJRNHCTCZ6FGFT4KMLJYUYWXRJRMXCTCYOFGFV4KMLFYUYWXRJRNHCTCZ6FGFU4KMLNYUYWLRJRNPCTC26FGFS4KMLJYUYWPRJRM7CTC2OFGFV4KMLFYUYWLRJRMXCTCZOFGFR4KMLJYUYWPRJRNPCTCYOFGFS4KMLNYUYWDRJRMXCTCZOFGFQ4KMLHYUYWTRJRNPCTCZOFGFQ4KMLLYUYWLRJRNPCTC2OFGFT4KMLJYUYW3RJRMXCTC26FGFV4KMLFYUYWTRJRM7CTCZ6FGFU4KMLNYUYWLRJRNXCTCZ6FGFS4KMLFYUYWXRJRM7CTC2OFGFW4KMLFYUYW3RJRMXCTCZOFGFX4KMLHYUYWPRJRNHCTC26FGFS4KMLBYUYWXRJRMXCTC26FGFU4KMLHYUYWTRJRNXCTCZOFGFV4KMLLYUYWLRJRNHCTCZ6FGFT4KMLJYUYWXRJRMXCTC36FGFR4KMLFYUYW3RJRM7CTCZ6FGFU4KMLPYUYWLRJRNPCTC26FGFS4KMLDYUYWHRJRM7CTC2OFGFV4KMLFYUYWDRJRNPCTCZOFGFV4KMLJYUYWPRJRNHCTC3OFGFS4KMLLYUYWXRJRMXCTC2OFGFT4KMLHYUYWXRJRMHCTCZOFGFQ4KMLPYUYWLRJRNPCTCZOFGFT4KMLJYUYW7RJRMXCTCZOFGFU4KMLFYUYW3RJRMPCTCZ6FGFU4KMLNYUYWLRJRMXCTC3OFGFS4KMLBYUYW7RJRM7CTC2OFGFW4KMLFYUYWPRJRMHCTCZOFGFR4KMLNYUYWPRJRNPCTCYOFGFS4KMLLYUYW7RJRMXCTCZ6FGFS4KMLHYUYWTRJRNHCTCZOFGFX4KMLPYUYWLRJRNHCTCY6FGFT4KMLJYUYWXRJRMXCTCZOFGFS4KMLFYUYWHRJRNHCTCZ6FGFV4KMLBYUYWLRJRNXCTCYOFGFS4KMLFYUYWDRJRM7CTC2OFGFV4KMLFYUYWLRJRMXCTCZOFGFR4KMLJYUYWPRJRNPCTCYOFGFS4KMLNYUYWDRJRMXCTCZOFGFQ4KMLHYUYWTRJRNXCTCZOFGFS4KMLNYUYWLRJRMHCTC36FGFT4KMLJYUYW3RJRMXCTCZ6FGFQ4KMLFYUYWHRJRNXCTCZ6FGFU4KMLLYUYWLRJRMHCTC26FGFS4KMLLYUYWTRJRM7CTC2OFGFW4KMLFYUYWXRJRNPCTCZOFGFU4KMLHYUYWPRJRNHCTC26FGFS4KMLPYUYWHRJRMXCTC3OFGFT4KMLHYUYWTRJRN7CTCZOFGFV4KMLLYUYWLRJRMPCTCY6FGFT4KMLJYUYWXRJRMXCTCYOFGFV4KMLFYUYWXRJRNHCTCZ6FGFU4KMLNYUYWLRJRNPCTC26FGFS4KMLJYUYWPRJRM7CTC2OFGFV4KMLFYUYWDRJRNPCTCZOFGFV4KMLJYUYWPRJRNHCTC3OFGFS4KMLLYUYWXRJRMXCTC2OFGFT4KMLHYUYWTRJRNPCTCZOFGFS4KMLFYUYWLRJRMPCTC2OFGFT4KMLLYUYWDRJRMXCTC3OFGFQ4KMLFYUYWLRJRMHCTCZ6FGFU4KMLNYUYWLRJRMXCTC26FGFS4KMLLYUYWTRJRM7CTC2OFGFU4KMLFYUYW7RJRMHCTCZOFGFT4KMLFYUYWPRJRNHCTC26FGFS4KMLFYUYWLRJRMXCTCY6FGFU4KMLHYUYWXRJRMHCTCZOFGFW4KMLBYUYWLRJRMXCTCYOFGFT4KMLLYUYWDRJRMXCTCYOFGFX4KMLFYUYWXRJRMXCTCZ6FGFU4KMLPYUYWLRJRMXCTC2OFGFS4KMLNYUYWHRJRM7CTC2OFGFV4KMLFYUYWDRJRNPCTCZOFGFV4KMLJYUYWPRJRNHCTC3OFGFS4KMLLYUYWXRJRMXCTC2OFGFT4KMLHYUYWTRJRNPCTCZOFGFQ4KMLLYUYWLRJRNPCTC2OFGFT4KMLJYUYW3RJRMXCTC26FGFV4KMLFYUYWTRJRM7CTCZ6FGFU4KMLNYUYWLRJRNXCTCZ6FGFS4KMLFYUYWXRJRM7CTC2OFGFW4KMLFYUYW3RJRMXCTCZOFGFX4KMLHYUYWPRJRNHCTC26FGFS4KMLDYUYW7RJRMXCTCY6FGFT4KMLHYUYWTRJRNPCTCZOFGFS4KMLNYUYWLRJRMHCTC2OFGFT4KMLJYUYW3RJRMXCTC3OFGFT4KMLFYUYWLRJRNPCTCZ6FGFU4KMLNYUYWLRJRNXCTCZOFGFS4KMLPYUYWPRJRM7CTC2OFGFV4KMLFYUYWDRJRNPCTCZOFGFV4KMLJYUYWPRJRNHCTC3OFGFS4KMLLYUYWXRJRMXCTC2OFGFT4KMLHYUYWTRJRNXCTCZOFGFS4KMLLYUYWLRJRNPCTC2OFGFT4KMLJYUYWTRJRMXCTC36FGFQ4KMLFYUYWPRJRMXCTCZ6FGFU4KMLNYUYWLRJRNXCTCZ6FGFS4KMLFYUYWXRJRM7CTC2OFGFW4KMLFYUYW3RJRMXCTCZOFGFX4KMLHYUYWPRJRNHCTC26FGFS4KMLDYUYW7RJRMXCTCY6FGFT4KMLHYUYWTRJRNPCTCZOFGFS4KMLNYUYWLRJRMHCTC2OFGFT4KMLJYUYWXRJRMXCTC36FGFR4KMLFYUYW3RJRM7CTCZ6FGFU4KMLPYUYWLRJRNPCTC26FGFS4KMLDYUYWHRJRM7CTC2OFGFV4KMLFYUYWDRJRNPCTCZOFGFV4KMLJYUYWPRJRNHCTC3OFGFS4KMLLYUYWXRJRMXCTC2OFGFT4KMLHYUYWTRJRNXCTCZOFGFW4KMLBYUYWLRJRMXCTCY6FGFT4KMLJYUYWTRJRMXCTC36FGFQ4KMLFYUYW7RJRM7CTCZ6FGFU4KMLLYUYWLRJRMXCTCZOFGFS4KMLDYUYWTRJRM7CTC26FGFQ4KMLFYUYW3RJRMHCTCZOFGFS4KMLBYUYWPRJRNHCTC3OFGFS4KMLNYUYWPRJRMXCTCZOFGFV4KMLHYUYWTRJRNXCTCZOFGFW4KMLFYUYWLRJRN7CTCZ6FGFT4KMLJYUYW3RJRMXCTCZOFGFW4KMLFYUYWDRJRN7CTCZ6FGFU4KMLNYUYWLRJRM7CTCYOFGFS4KMLDYUYW3RJRM7CTC26FGFQ4KMLFYUYWXRJRN7CTCZOFGFT4KMLFYUYWPRJRNHCTC2OFGFS4KMLPYUYW7RJRMXCTC2OFGFR4KMLHYUYWTRJRNPCTCZOFGFS4KMLFYUYWLRJRMPCTC2OFGFT4KMLLYUYWDRJRMXCTC3OFGFQ4KMLFYUYWLRJRMHCTCZ6FGFU4KMLLYUYWLRJRMXCTCZOFGFS4KMLDYUYWTRJRM7CTC26FGFQ4KMLFYUYW3RJRMHCTCZOFGFS4KMLBYUYWPRJRNHCTC3OFGFS4KMLNYUYWDRJRMXCTCZOFGFR4KMLHYUYWTRJRNHCTCZOFGFX4KMLBYUYWLRJRN7CTCZ6FGFT4KMLJYUYWXRJRMXCTCZOFGFS4KMLFYUYWHRJRNHCTCZ6FGFV4KMLBYUYWLRJRNXCTCYOFGFS4KMLFYUYWDRJRM7CTC2OFGFX4KMLFYUYWHRJRMHCTCZOFGFW4KMLDYUYWPRJRNHCTC26FGFS4KMLHYUYWPRJRMXCTC36FGFV4KMLHYUYWTRJRNXCTCZOFGFS4KMLNYUYWLRJRMHCTC36FGFT4KMLJYUYW3RJRMXCTCZ6FGFQ4KMLFYUYWHRJRNXCTCZ6FGFV4KMLBYUYWLRJRNPCTC36FGFS4KMLHYUYWLRJRM7CTC2OFGFU4KMLFYUYW7RJRN7CTCZOFGFU4KMLDYUYWPRJRNHCTC26FGFS4KMLFYUYWLRJRMXCTCY6FGFU4KMLHYUYWXRJRMHCTCZOFGFW4KMLBYUYWLRJRMXCTCYOFGFT4KMLJYUYWXRJRMXCTCZOFGFS4KMLFYUYWHRJRNHCTCZ6FGFV4KMLBYUYWLRJRNXCTCYOFGFS4KMLFYUYWDRJRM7CTC2OFGFW4KMLFYUYW3RJRMHCTCZOFGFS4KMLDYUYWPRJRNHCTC2OFGFS4KMLPYUYWDRJRMXCTC36FGFT4KMLHYUYWTRJRNPCTCZOFGFS4KMLFYUYWLRJRMPCTC2OFGFT4KMLLYUYWDRJRMXCTC3OFGFQ4KMLFYUYWLRJRMHCTCZ6FGFU4KMLNYUYWLRJRMXCTC3OFGFS4KMLBYUYW7RJRM7CTC2OFGFW4KMLFYUYWPRJRMHCTCZOFGFR4KMLNYUYWPRJRNHCTC26FGFS4KMLBYUYWXRJRMXCTC26FGFU4KMLHYUYWTRJRNXCTCZOFGFV4KMLLYUYWLRJRNHCTCZ6FGFT4KMLJYUYWXRJRMXCTCY6FGFX4KMLFYUYWHRJRM7CTCZ6FGFU4KMLLYUYWLRJRMXCTC3OFGFS4KMLBYUYWTRJRM7CTC2OFGFX4KMLFYUYWHRJRMHCTCZOFGFW4KMLDYUYWPRJRNHCTC26FGFS4KMLHYUYWPRJRMXCTC36FGFV4KMLHYUYWTRJRNPCTCZOFGFS4KMLFYUYWLRJRMPCTC@OFGFT4KMLLYUYWDRJRMXCTC3OFGFQ4KMLFYUYWLRJRMHCTCZ6FGFU4KMLPYUYWLRJRMPCTCYOFGFS4KMLNYUYWHRJRM7CTC2OFGFV4KMLFYUYWPRJRM7CTCZOFGFX4KMLLYUYWPRJRNHCTC26FGFS4KMLFYUYWLRJRMXCTCY6FGFU4KMLHYUYWXRJRMHCTCZOFGFW4KMLBYUYWLRJRMXCTCYOFGFT4KMLJYUYW3RJRMXCTC3OFGFQ4KMLFYUYWLRJRMPCTCZ6FGFU4KMLJYUYWLRJRN7CTCYOFGFS4KMLPYUYWPRJRM7CTC2OFGFV4KMLFYUYWDRJRNPCTCZOFGFV4KMLJYUYWPRJRNHCTC3OFGFS4KMLLYUYWXRJRMXCTC2OFGFT4KMLHYUYWTRJRNPCTCZOFGFS4KMLFYUYWLRJRMPCTC2OFGFT4KMLLYUYWDRJRMXCTC3OFGFQ4KMLFYUYWLRJRMHCTCZ6FGFU4KMLLYUYWLRJRMHCTC26FGFS4KMLLYUYWTRJRM7CTC@OFGFW4KMLFYUYWXRJRNPCTCZOFGFU4KMLHYUYWPRJRNHCTC26FGFS4KMLPYUYWHRJRMXCTC3OFGFT4KMLHYUYWTRJRN7CTCZOFGFV4KMLLYUYWLRJRMPCTCYQ==== |
抽象,陌生。
有几个特殊字符“@,$,&”
试了一下,@改成Y,$改成S,&改成P可以用base32解出八卦符号
☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☶☲☲☶☲☰☷☳☴☶☲☳☰☲☱☶☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☷☱☲☶☳☳☴☷☲☵☵☲☱☱☳☴☶☲☲☶☲☰☷☳☴☶☲☳☰☲☱☶☳☴☵☲☱☷☲☱☳☳☴☵☲☲☶☲☰☴☳☴☶☲☶☳☲☲☵☳☴☶☲☶☲☲☷☳☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☶☲☶☳☲☲☵☳☴☶☲☶☲☲☷☳☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☶☲☲☶☲☰☷☳☴☶☲☳☰☲☱☶☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☷☱☲☶☳☳☴☷☲☵☵☲☱☱☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☷☱☲☶☳☳☴☷☲☵☵☲☱☱☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☷☲☱☰☲☶☱☳☴☵☲☳☳☲☷☵☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☷☱☲☶☳☳☴☷☲☵☵☲☱☱☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☵☰☲☰☵☲☵☲☳☴☷☲☲☴☲☶☱☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☷☲☱☰☲☶☱☳☴☵☲☳☳☲☷☵☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☵☲☵☷☲☱☴☳☴☵☲☵☴☲☷☲☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☷☲☱☰☲☶☱☳☴☵☲☳☳☲☷☵☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☶☲☶☳☲☲☵☳☴☶☲☶☲☲☷☳☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☷☱☲☶☳☳☴☷☲☵☵☲☱☱☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☵☰☲☰☷☲☵☲☳☴☷☲☲☴☲☶☱☳☴☶☲☲☶☲☰☷☳☴☶☲☳☰☲☱☶☳☵☰☲☵☷☲☳☲☳☴☴☲☷☷☲☴☱☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☶☲☲☶☲☰☷☳☴☶☲☳☰☲☱☶☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☷☱☲☶☳☳☴☷☲☵☵☲☱☱☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☶☲☲☵☲☵☴☳☴☴☲☷☰☲☳☲☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☵☰☲☰☷☲☵☲☳☴☷☲☲☴☲☶☱☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☶☲☶☳☲☲☵☳☴☶☲☶☲☲☷☳☳☴☵☲☱☷☲☱☳☳☴☵☲☲☶☲☰☴☳☴☶☲☶☳☲☲☵☳☴☶☲☶☲☲☷☳☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☶☲☲☵☲☵☴☳☴☴☲☷☰☲☳☲☳☴☶☲☶☳☲☲☵☳☴☶☲☶☲☲☷☳☳☴☵☲☱☷☲☱☳☳☴☵☲☲☶☲☰☴☳☴☵☲☷☱☲☶☳☳☴☷☲☵☵☲☱☱☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☶☲☶☰☲☲☱☳☴☴☲☷☰☲☷☳☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☶☲☶☳☲☲☵☳☴☶☲☶☲☲☷☳☳☴☶☲☲☶☲☰☷☳☴☶☲☳☰☲☱☶☳☵☰☲☵☷☲☳☲☳☴☴☲☷☷☲☴☱☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☶☲☶☰☲☲☱☳☴☴☲☷☰☲☷☳☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☷☲☱☰☲☶☱☳☴☵☲☳☳☲☷☵☳☴☶☲☲☶☲☰☷☳☴☶☲☳☰☲☱☶☳☵☰☲☵☷☲☳☲☳☴☴☲☷☷☲☴☱☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☶☲☶☰☲☲☱☳☴☴☲☷☰☲☷☳☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☶☲☲☶☲☰☷☳☴☶☲☳☰☲☱☶☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☱☷☲☱☳☳☴☵☲☲☶☲☰☴☳☴☷☲☱☰☲☶☱☳☴☵☲☳☳☲☷☵☳☴☵☲☲☲☲☱☰☳☵☰☲☶☰☲☲☰☳☴☷☲☱☰☲☶☱☳☴☵☲☳☳☲☷☵☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☶☲☶☰☲☲☱☳☴☴☲☷☰☲☷☳☳☴☵☲☰☵☲☵☴☳☴☶☲☵☵☲☴☳☳☴☵☲☲☲☲☱☴☳☵☰☲☶☰☲☲☰☳☴☵☲☰☵☲☵☴☳☰☶☲☵☵☲☴☳☳☴☵☲☷☱☲☶☳☳☴☷☲☵☵☲☱☱ |
对于卦象有如下理解,(不唯一,可以每种都试试)
'☰':'0', # 乾 |
数字3个一组,组合成八进制,然后转文本就可以了。附上脚本,有一点是上属特殊字符替换导致原数据异常,无法直接解码,所以我是记事本查找替换得到的结果
def to8bArr(baguaStr): |
公正文明公正和谐公正平等文明友善法治和谐法治公正文明公正平等公正平等和谐爱国公正平等和谐和谐公正自由和谐爱国和谐富强和谐爱国公正公正公正和谐公正法治公正平等公正自由文明诚信和谐和谐文明公正平等公正公正和谐敬业和谐自由公正公正法治友善法治公正敬业法治友善平等公正民主和谐法治文明诚信和谐和谐民主和谐爱国文明诚信和谐和谐民主和谐文明公正友善爱国和谐爱国和谐民主公正和谐公正平等 |
用在线工具直接转就好
bce-7bee8e3d808fcged-2ef94f}i{a7-18-12n81ce |
栅栏解密
begin{eec8da87-ee32-11ed-8f8c-907841e2ffbc} |
where is crazyman1.0

好大三个字秋叶原,我直接begin{秋叶原}
where is crazyman2.0

说实话刚开始搜的都是长隆海洋王国。。后来谷歌识图直接找到了Boulevard World,那么就是begin{Boulevard World}
Crypto
fuck_n
from Crypto.Util.number import * |
fake_n是17个素数(15个32bits的素数和1个64bits的合数)
really_n是15个素数的乘积,直接遍历即可
from factordb.factordb import FactorDB |
OEIS2
和2023强网杯的speed up一样,但是比强网杯恶心,$(2^{28}+5)!$的各位和,查表可以得到一部分但是没什么用,可能是我没找对,sage直接跑!
#sage |
我是玩青水的
from Crypto.Util.number import * |
e = 2的rsa加密,当我用正常脑子解题,解不出来。试试低加密指数攻击
import gmpy2 |
*hard_ECC
from flag import flag |
Q = T * secret,解secret
#Sage Code 1 |
栅栏解密
begin{it_is_hard?} |
*PAD
import random, math |
分析加密过程可知
整合一下
已知$pad.e$和$self.e$分别是(2,7)和(1,8)之间取值,恰好当$pad.e = 2$,$self.e = 1$时有以下式子
现在就很容易解了,直接给$c-2^{512}$开方即可
在gift中找到如下数据
self.n = 105489743033600776618404736924014082773234739025040235918547880079849719971737127359304073614094075884043630513694448370483208184306027684643273284267932051217742004175757404293643624264846421545917186078199365762796141089940330731024030929168374696605389962930325106070659194496163327222019090112724836643593 |
from Crypto.Util.number import * |
特殊值。。这算是非预期吗。。。
*PAD_revenge
from Crypto.Util.number import * |
算法和上个PAD没区别,只是多了个条件,避免了上题的开方出结果。
现在两个e都是(1,9)取值,在gift中找三段$pad.e = 3$和$self.e = 1$的结果,就可以用中国剩余定理解出
找到可用数据如下
(4205338792881421548510609645647062608905484696099258750943039118994520455106270839395319116980996505132271552239717225130972438536887110724158402296232289, 1, (3, 590242556810530557883636062945321456666605165279521102134969558150863508014273375308372904949297413593224978273122299933502842450872249868557340596692448)) |
#sage |
对上述值开3次方
import gmpy2 |
还有另一种解法,Hastad’s Attack,传送门:BeginCTF | DexterJie’Blog
*Baph
from base64 import b64encode |
与CryptoCTF2021的Baph类似,那个相对简单些。
加密过程如下
flag----base64---->ba |
exp:
from Crypto.Util.number import * |
*baby_classic
from random import * |
加密过程:
$k1,k2$未知,$k1$是位置的66密钥矩阵,每个元素都是模29下的随机数。$k2$是$1 6$的加密矩阵2。
题目给出了长度为48的已知明文m,密文c,并且给出长度为72的ciphertext,要求我们解出ciphertext对应的明文。
对于已知明文和密文,有以下式子
把上式拆分成8个形如下式的矩阵方程:
我们任取其中两个矩阵方程,作差,就可以把K2消掉,得到:
八组数据可以作出七组线性无关的差,重新组成一个矩阵方程。对于K1来说,只需要六组数据就可以达到满秩,因此可以求出$K1$。
解出$K1$后代入任意一组就可以解出$K2$,然后就可以求出ciphertext对应的明文。
from string import * |
*ezcry
不会。这使我小脑萎缩
学会补
*begin_rsa
不会。这使我小脑萎缩.
学会补
WEB
解了四个文件上传,前因后果一概不知,就不献丑了。。
re
real checkin xor
没什么含金量,签到题,简单异或,key也给了
def verify_func(ciper,key): |
Forensics
逆向工程
下载附件“ctrl+f”,直接搜,还是透明的6
begin{0kay_1_thiNK_YoU_Ar3_a1Re@DY_rE4D_6uiDe8ooK_AnD_9OT_FL46} |
学取证喽-cmd
kali下载好volatility后
下载教程
volatility2
https://blog.csdn.net/Aluxian_/article/details/128194996?spm=1001.2014.3001.5506
volatility3
https://blog.csdn.net/Aluxian_/article/details/127064750?spm=1001.2014.3001.5506
直接输入指令
python2 vol.py -f 1.raw --profile=Win7SP1x64 cmdscan |
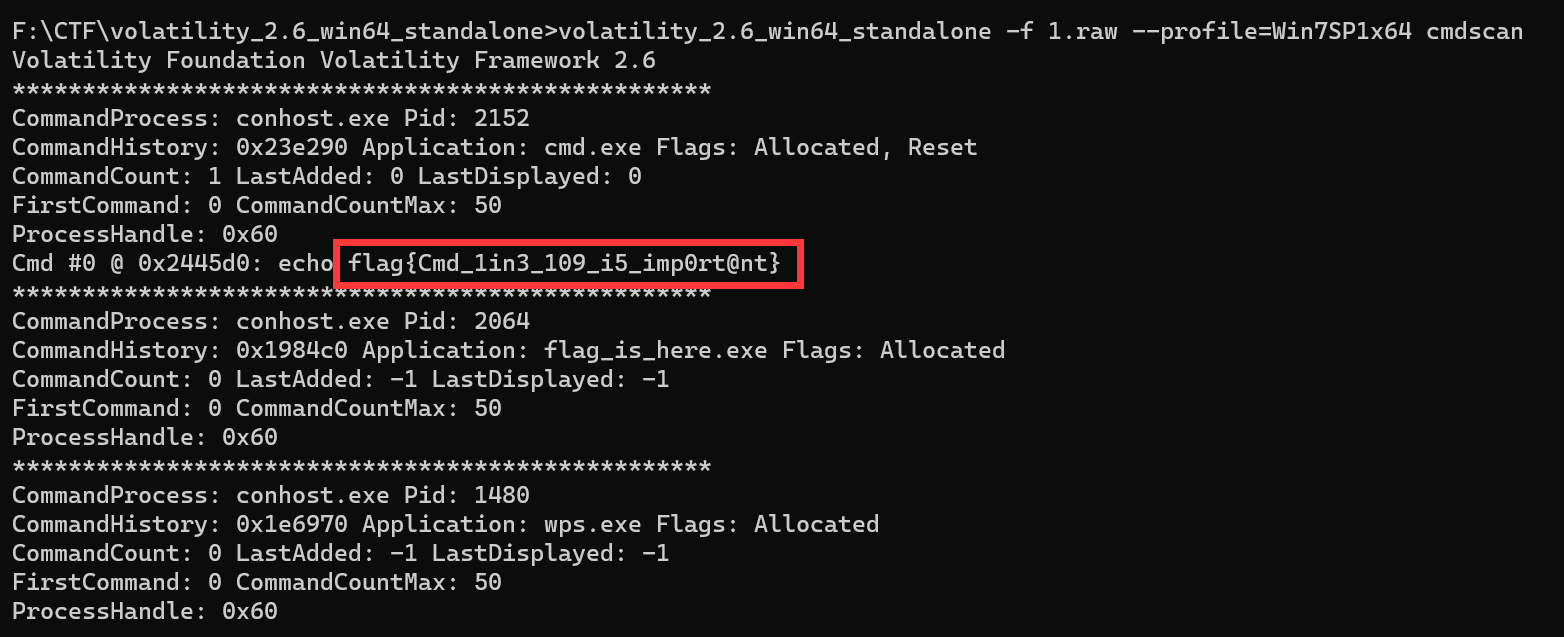
学取证喽-浏览器记录
python2 vol.py -f 1.raw --profile=Win7SP1x64 iehistory |
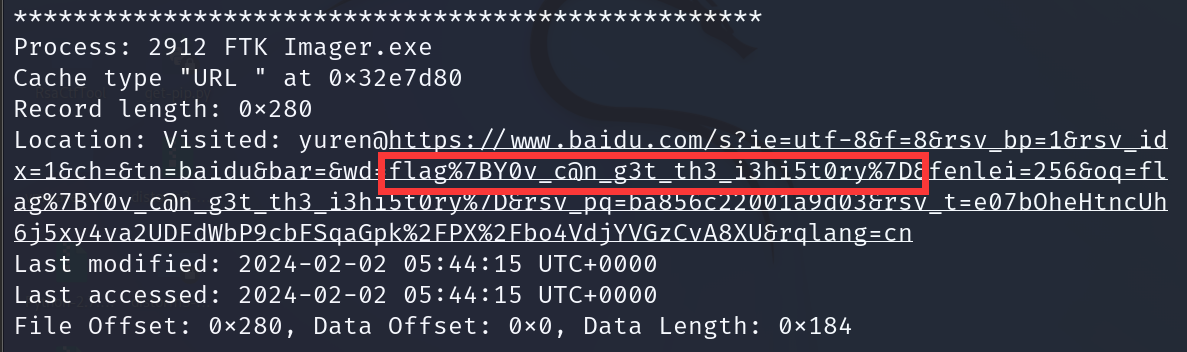
学取证喽-计算机名
python2 vol.py -f 1.raw --profile=Win7SP1x64 printkey -K "ControlSet001\Control\ComputerName\ComputerName" |
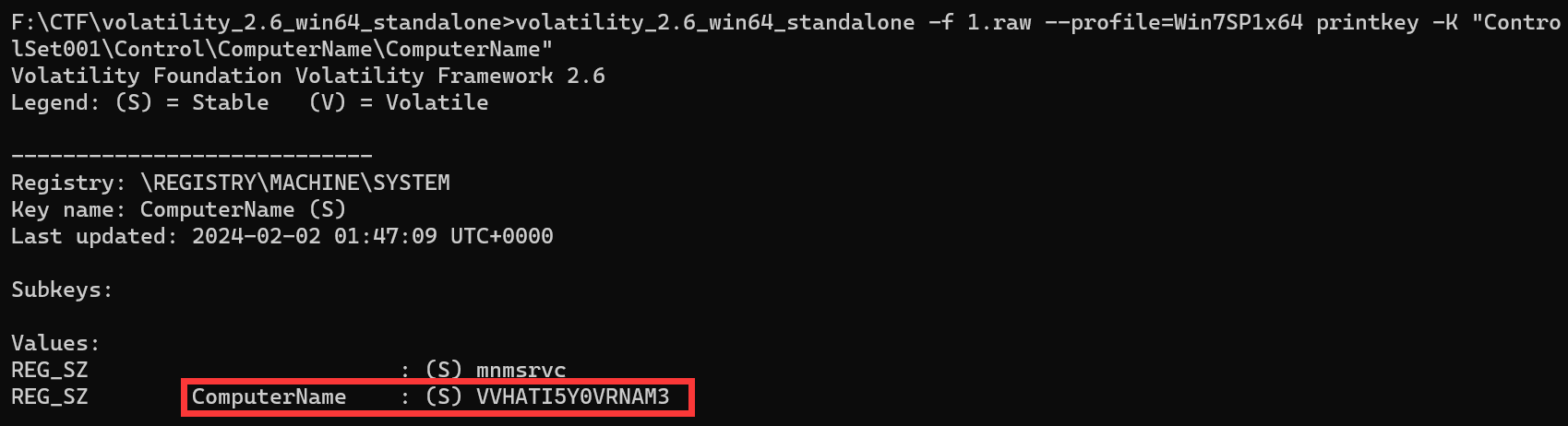
begin{VVHATI5YOVRNAM3} |
学取证喽-登录密码
python2 vol.py -f 1.raw --profile=Win7SP1x64 mimikatz |
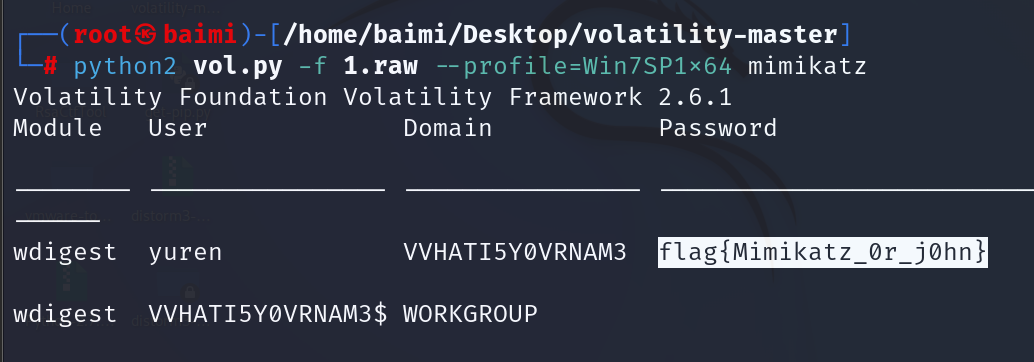
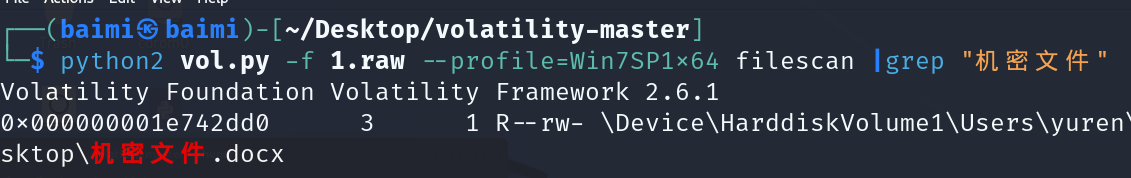
学取证喽-机密文件
python2 vol.py -f 1.raw --profile=Win7SP1x64 filescan |grep "机密文件" |
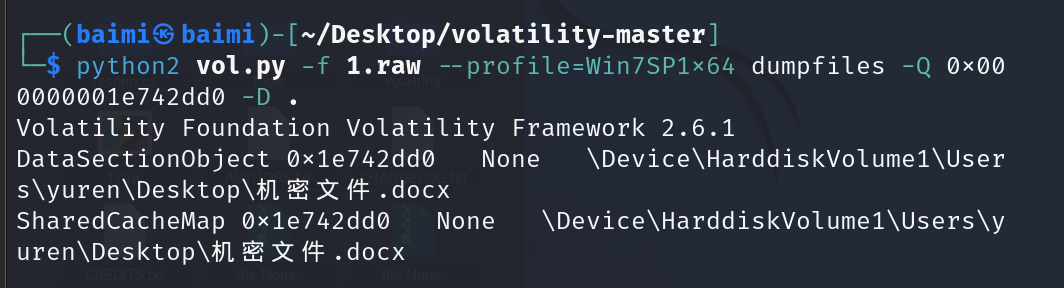
把上述文件提取
python2 vol.py -f 1.raw --profile=Win7SP1x64 dumpfiles -Q 0x000000001e742dd0 -D . |
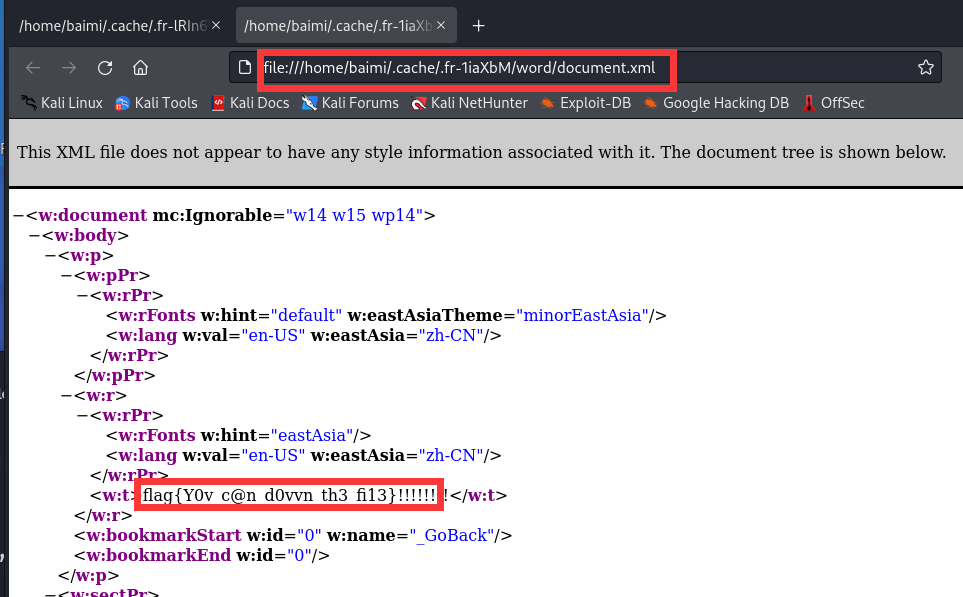
打开文件找到/word/document.xml就找到了flag
后续还会复现剩下的Crypto题目,待续。。
复现参考文章:
BeginCTF 2024 夺旗赛 Crypto 方向个人题解 | Linmu’s murmur (linmur.top)
师傅们的思路还要学习啊,我好菜





